Table of Contents
Introduction – Imagine Talking to Your Computer from Far Away
Let’s start with a simple question:
What if you could sit in your room and control a computer in New York, Tokyo, or your friend’s basement with just a few keystrokes?
Sounds like something out of a sci-fi movie, right?
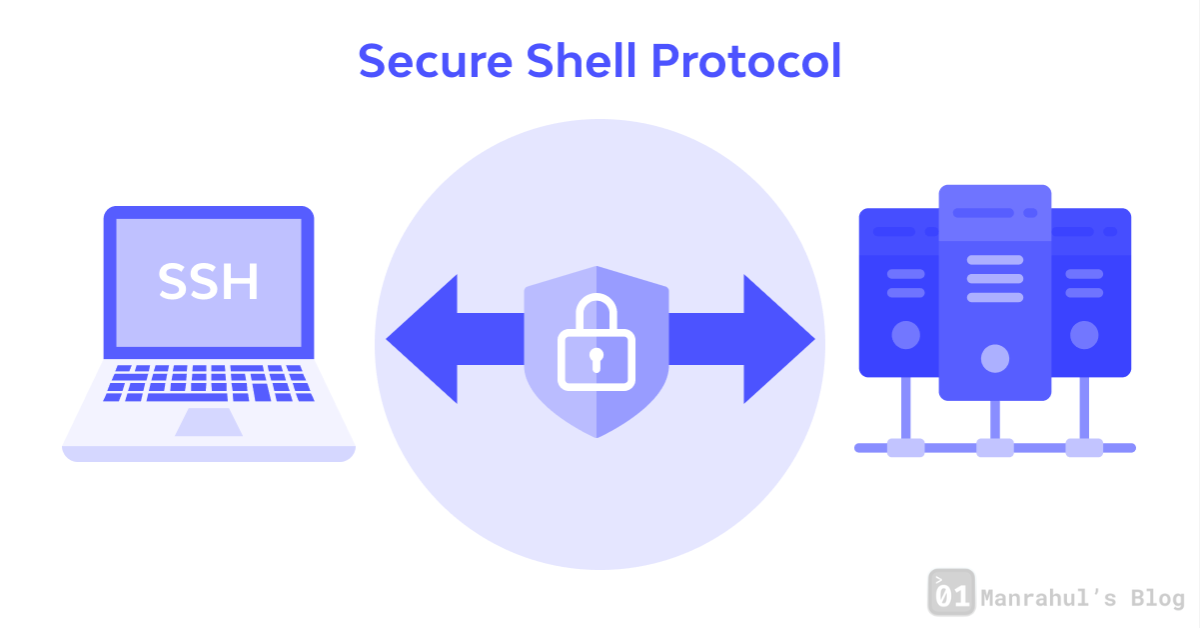
Well, that’s exactly what SSH (Secure Shell) lets you do — in a very real, secure, and professional way.
If you’ve read my blog on Linux Permissions or Virtualization, you already know how powerful Linux is. SSH is another core tool in your Linux toolkit.
The Problem Before SSH: The Wild West of Remote Access
Back in the early internet days, we had tools like Telnet. It let people connect to remote computers…
BUT it sent all data, including passwords, in plain text.
Yup — if someone was “sniffing” your network, they could literally see your login and commands.
Problem:
No encryption. No security. Easy to hack.
The Birth of SSH: A Safer Way to Say Hello
In 1995, a guy named Tatu Ylönen developed SSH as a secure replacement for Telnet.
SSH stands for Secure Shell.
- “Secure” because it encrypts everything.
- “Shell” because it gives you command-line access to the remote system.
Now people could safely manage servers, transfer files, and run scripts — all from miles (or continents) away.
So… What Does SSH Actually Do?
Let’s get real here. SSH is not some fancy app.
It’s a simple tool that lets you connect to another machine via command line — securely.
Here’s a mental image:
You (in your terminal): “Hey remote server, can I come in?”
Server: “Sure, just prove you’re you.”
You give your username and password or SSH key.
🎉 Boom! You’re now inside the server. You can control it like it’s your own.
A Real Example (This is where it gets cool)
Let’s say your friend has a Raspberry Pi running Linux at home. You can connect to it like this:
ssh [email protected]Here’s what it means:
ssh: the commandpi: the username on the other machine192.168.1.50: the IP address of the remote machine
You enter the password, and now you’re controlling the Pi from your laptop. Just like magic.
What Can You Do With SSH?
Oh, so much. Here’s what SSH allows:
- Access and manage remote servers (for websites, apps, or backups)
- Transfer files securely with
scporrsync - Tunnel connections (like accessing databases behind firewalls)
- Run remote commands or automate deployments
- Fix a crashed app in production at 2am (Been there!)
Deep Dive: How SSH Works (Visually & Technically)
Here’s the flow in a nutshell:
- You open terminal and type:
ssh user@host - SSH tries to establish a connection on port 22
- You authenticate with a password or SSH key
- If valid, the server grants you a secure encrypted shell session
- Every command you now type is run on that remote machine
Bonus: Use an SSH key pair (like a lock and key) to avoid typing passwords every time.
SSH Keys – The Secret Sauce for Pro Users
Passwords are okay. But pros use SSH Keys for faster, safer access.
You generate a key pair:
ssh-keygenYou’ll get:
- A private key (
id_rsa) – keep this secure. - A public key (
id_rsa.pub) – you can share this.
You copy the public key to your server like this:
ssh-copy-id user@remotehostNow, you can log in without a password!
Real-Life Uses of SSH
- Managing a VPS (cloud server)
- Accessing a home media server from college
- Automating backups every night
- Fixing bugs in live apps
- Transferring huge files securely
Common SSH Commands You’ll Actually Use
| Command | What It Does |
|---|---|
ssh user@host | Connect to remote system |
scp file user@host:/path/ | Copy file to remote |
rsync -av file user@host:/path/ | Sync folders |
ssh -i key.pem user@host | Connect using a specific SSH key |
ssh -p 2222 user@host | Connect using custom port |
Pro Tips (From My Experience)
- Always use SSH keys, never rely on passwords alone.
- Change your server’s SSH port to reduce bot attacks (e.g. use 2222 instead of 22).
- Use
fail2banor similar tools to block brute-force attempts. - Set up
~/.ssh/configto manage multiple servers easily.
Example:
Host myserver
HostName 192.168.1.50
User pi
Port 2222
IdentityFile ~/.ssh/id_rsa
Now just type:
ssh myserverThoughts
SSH might sound intimidating at first, but once you try it, it’s like learning to ride a bike — you’ll wonder how you lived without it.
For any developer, DevOps engineer, or even a student curious about Linux, SSH is one of the most important skills you can have.
And just like we explored in The Linux Boot Process, every system has a journey — SSH lets you jump into that journey from anywhere in the world.