Table of Contents
Why Should We Even Care About Permissions?
Imagine leaving your house door wide open, lights on, and your journal on the coffee table. Anyone passing by could walk in, read your stuff, and even mess things up. That’s what it’s like running a Linux system without proper file permissions.
Linux permissions are not just some technical fluff—they’re the digital equivalent of locks, keys, and “Do Not Enter” signs for your files, folders, and systems. And understanding them gives you power—the kind that lets you control who can do what.
But wait—where did this idea even come from?
From Multi-User Systems to Personal Machines
Linux comes from a Unix heritage, where systems were built to serve multiple users at the same time. Everyone had access to the same machine, but that didn’t mean they should have access to each other’s stuff.
To solve this, Unix introduced a permission system:
- Who owns a file?
- Who else can use it?
- What are they allowed to do?
This system made sure users didn’t accidentally—or intentionally—wreck each other’s work.
The Problem It Solves
Let’s keep it simple. Here are some real-world scenarios:
- You want to share a file, but only let others read it—not modify it.
- You want a script to be executable, but not editable by others.
- You want to hide sensitive files from unauthorized users.
Without permissions, any user (or app) could read, edit, or delete anything.
The Basics: Read, Write, Execute
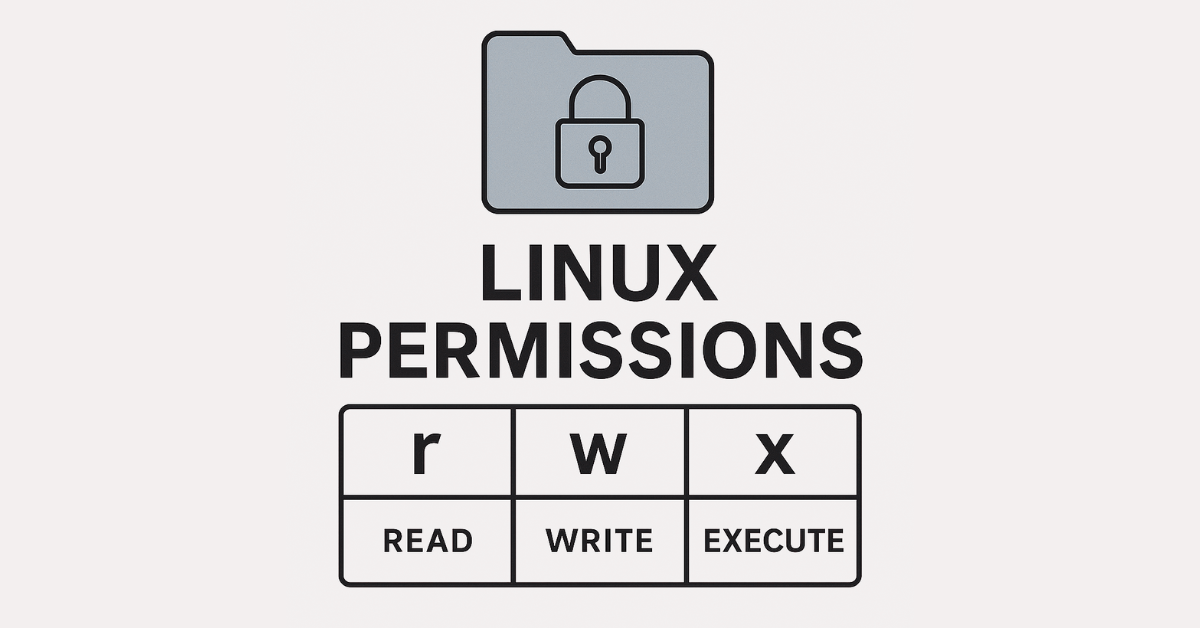
Every file and directory in Linux has three types of access permissions:
| Symbol | What It Means | Applies To… |
r | Read | Can view the contents |
w | Write | Can modify or delete |
x | Execute | Can run the file (if it’s a program/script) or access a directory |
But permissions are not just what you can do, but also who can do it.
Who’s Allowed?
Each file has three sets of permissions:
- User (u) — the owner of the file
- Group (g) — a group of users
- Others (o) — everyone else
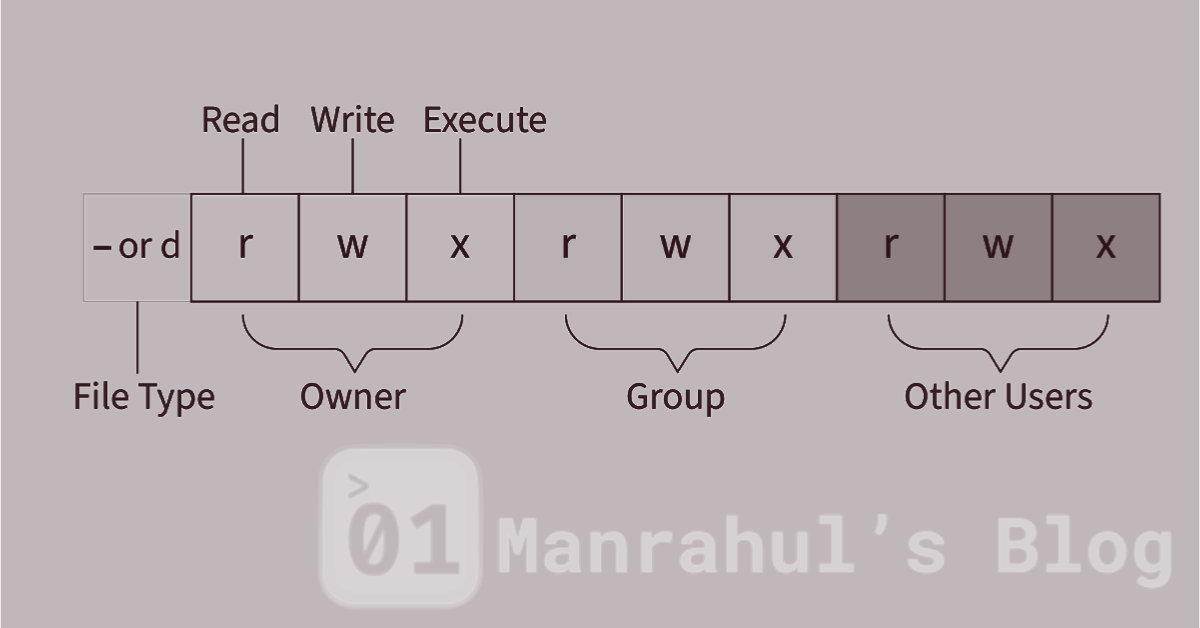
So a permission string like this: diff Copy Edit
-rwxr-xr--…translates to:
- User: read, write, execute
- Group: read, execute
- Others: read only
Looks not understandable? but It’s really not. Once you see the pattern, it becomes so relatable easy.
How to See It in Action?
Run this in your terminal:
ls -l
Output:
-rw-r--r-- 1 manrahul devs 1200 May 20 10:12 notes.txt
Breakdown – Let’s understand this:
-rw-r--r--: The permissionsmanrahul: The file ownerdevs: The groupnotes.txt: The file name
This tells us:
- Manrahul can read and write it
- Devs group can only read it
- Others can also only read it
Changing Permissions Explore chmod, chown, and chgrp
Let’s say you’ve got a script backup.sh, and you want to make it executable.
chmod +x backup.sh
If we want to give only the owner read/write/execute
chmod 700 backup.sh
This uses numeric mode:
- 7 = read + write + execute
- 6 = read + write
- 5 = read + execute
- 4 = read
So:
chmod 755means: owner can do everything, others can read & executechmod 644: owner can read/write, others can only read
Ownership Who’s the Owner?
Changing the owner:
chown manrahul backup.sh
Changing the group:
chgrp devs backup.sh
This is especially useful on multi-user systems, shared folders, or servers.
Permissions on Directories Work Slightly Differently
For directories, the meanings change a bit:
r→ Can list files in the directoryw→ Can add or delete files from the directoryx→ Can enter the directory (cd into it)
So if a user has no x on a directory, they can’t even access its contents.
The Problem of 777 – A Permission Problem
Many beginners fall into this trap:
chmod 777 somefile
This gives everyone read, write, and execute access. You’re basically saying:
“Hey hackers, do what you like!”
It might fix a permission issue quickly, but it’s dangerous and bad practice in real environments.
Real Life Analogy (Because Why Not?)
Think of your Linux filesystem like a shared house:
- You (user) own your room (files).
- Your roommates (group) may have access to the common area (shared directories).
- Strangers (others) might only be allowed into the hallway, or not at all.
Permissions = house rules. They keep the house running smoothly without problems.
Why This Matters (Especially for Developers)
Whether you’re a developer deploying code, a sysadmin managing servers, or a curious learner:
- Understanding permissions helps you troubleshoot faster
- Keeps your systems secure
- Avoids “it works on my machine” nightmares
Once you truly understand Linux permissions, you stop fearing the terminal, and start controlling it confidently.
Personal Thought From Developer
I saw many developers using 777 permission for this quick fix, It’s a psychology. New learners want to get rid of errors without understanding what they are doing.
Linux permissions are not something you memorize – they’re something you feel. You use them daily without even realizing it.
So next time you type chmod, you’ll know you’re not just running a command.
You’re giving necessary permissions for a reason. Use them wisely.
Resources & Further Reading
- The Linux Documentation Project – File Permissions
A beginner-friendly intro to understanding file ownership and permissions in Linux. - GNU Coreutils Manual:
chmod
Official documentation for thechmodcommand — the tool used to change permissions. - Ubuntu Official Docs – Understanding Permissions
Clear examples and explanations from Ubuntu’s help docs. - Wikipedia – File system permissions
Covers file permissions broadly across Linux, Unix, and Windows systems. - chmod Calculator (Online Tool)
Handy web tool to convert symbolic (rwx) to numeric (755,644) and vice versa.


am learning docker and linux